Rockyoutxt Password List Download
Rockyou.txt is a big word list. Do they have to change their password often? I use all of these. The ones you download tend to be full of junk. May 18, 2015 - 1 Password dictionaries; 2 Leaked passwords. Rockyou, rockyou.txt.bz2 (60,498,886 bytes), n/a, 2009-12, Best list available; huge, stolen.
Random Theory Thoughts: If it is an AP with a default ESSID odds are the password is still default and pretty much impossible to crack with a word list. If the AP has been named something then odds are that it has a dictionary attack capable password. The password could contain entropy. Meaning it could be PASSWORD but with padding like P.A.S.S.W.O.R.D. The weakest Password just became strong and off your list. Something to think about.
Some AP's have a secret (the same) PIN that is issued to every AP of that vendor. Hi I am trying this to open a protected.rar file with cRARK in Kali Linux. My password length is 10 to 13.

I am executing the command./crark -c -l10 -g13 /root/desktop.rar file. And I partially remember the password. So I modified password.def file as ## abilnopr * ABINLNOPR * 1257 * 1257 abilnopr * 1257 ABILNOPR * abilnopr 1257 * ABILNOPR 1257 * ABILNOPR abilnopr 1257 $! * It taking more than a day to execute, But the password contains roop together, Is possible to mention somewhere and continue the search? Hi I am trying this to open a protected.rar file with cRARK in Kali Linux. My password length is 10 to 13. I am executing the command./crark -c -l10 -g13 /root/desktop/file.rar file.
And I partially remember the password. Nepali film dhadkan mp3 song download. So I modified password.def file as ## abilnopr * ABINLNOPR * 1257 * 1257 abilnopr * 1257 ABILNOPR * abilnopr 1257 * ABILNOPR 1257 * ABILNOPR abilnopr 1257 $! * It taking more than a day to execute, But the password contains 'roop' together & '15', Is possible to mention somewhere and continue the search?
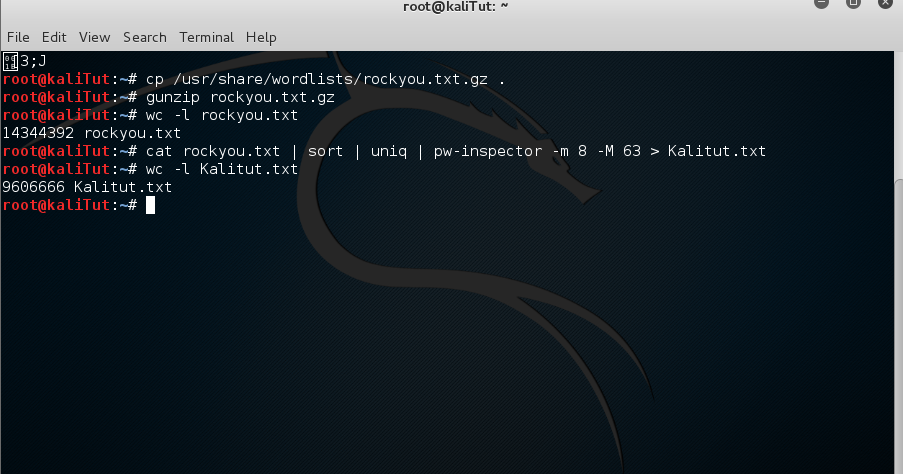
Posted on Updated on This post concentrates on password cracking using Hashcat. It describes various Hashcat rule sets, which can maximise the potential amount of cracked passwords utilising basic wordlists. The practical demonstration utilises pre-made rule sets, included in Hashcat directory by default. The practical demonstration does not utilise Hashcat algorithm functions such as Combination, Toggle-Case, Brute-Force or Permutation, it only utilises Straight algorithm. THE SETUP This demonstration utilises three different wordlists: rockyou.txt —available by default in Kali located in /usr/share/wordlists/. Crackstation-human-only —available for download.
M3g9tr0n wordlist —available for download. Unlike other hash cracking tools, Hashcat uses CPU resources rather than GPU. The processor that is utilised for hash cracking is Intel(R) Core(TM) i7-4700MQ CPU @ 2.40GHz. The virtual machine where Kali runs is set to take advantage of all 4 cores however, I’m not sure how the virtual environment impacts the performance of the processor. There are 15 passwords which were chosen randomly.